Do you want to get into the penetration testing field? If yes, we are going to discuss how you can stop being a script-kiddie and become a good penetration tester. If you are reading this article, you are on a good way to become an expert in penetration testing.
The way has never been easy, but you can reach it if others have. But it depends on the energy and effort you are going to put into it.
Before we continue with this article, let us first see what penetration testing really is. because some are having confusion about penetration testing and ethical hacking.
You may like also to know, how to become an ethical hacker
What is penetration testing?
Penetration testing is a type of security testing that is used to test the security of an application. It is conducted to find a security risk that might be present in a system.
When a system is not secure, then it’s easy for an attacker to get into it. Security is normally an accidental error that occurs while developing a system.
why is penetration testing important?
You must understand that penetration testing is very important to ensuring system or network security. Also, penetration testing normally must evaluate the system’s ability in order to be protected.
Also, penetration testing must assure that only external or internal authorized users can access the system.
Then, penetration testing is important because:
- It provides evidence to suggest why it is important to increase investment in the security aspect of technology
- also, it estimates the volume of the attack
- It supports avoiding black hat attacks and also protects the original data.
- helps also to detect the weakness of the system
Pay attention: penetration testing necessitates not only knowledge of the tools used to test, but also knowledge of how to use them. But a real penetration tester must be able to proceed rigorously and detect the weaknesses of a system.
They must be able to identify the technology behind them and test every single door that might be open to attackers.
Also, it is important to inform yourself about the law and what you are allowed to do or not. According to the laws of your country, the computer laws are not the same.
First, check laws about privacy and surveillance: Nine eyes countries, Five eyes, and Fourteen Eyes. Always check if what you’re doing is legal. Even when it’s not offensive, information gathering can also be illegal!
The penetration tester not only discovers vulnerabilities that could be used by attackers. But also must be able to exploit those vulnerabilities, to assess what attackers might gain after a successful exploitation
How is penetration testing Beneficial?
While the practice of penetration testing is growing in popularity, it comes with benefits.
Identify and resolve system vulnerabilities: Penetration testing is when penetration testers put themselves in a hacker’s position. By staying on the pulse of the cybersecurity world and regularly approaching IT systems from a cybercriminal’s perspective, penetration testers can identify a wide range of vulnerabilities and weaknesses in the system.
Gain valuable insights into digital systems: Reports from penetration testing can provide valuable details about the network or system, its weak points, and how to strengthen it.
Establish trust with your clientele: A cyberattack or data breach negatively affects the confidence and loyalty of your customers, vendors, and partners.
Protection from financial damage: A simple breach of a security system may cause millions of dollars of damage. Penetration testing can protect the organization from such damages.
some vocabulary related to penetration testing
A penetration tester: is an ethical hacker who practices security and tests applications and systems to prevent intrusions or find vulnerabilities.
Reverse engineering: Reverse engineering, also called back engineering, is the process by which a man-made object is deconstructed to reveal its designs and architecture, or to extract knowledge from the object.
similar to scientific research, the only difference is that scientific research is about a natural phenomenon.
Social engineering: In the context of information security, it refers to the psychological manipulation of people into performing actions or divulging confidential information.
Security researcher: Someone who practices pen testing and browses the web to find phishing/fake websites, infected servers, bugs, or vulnerabilities.
They can work for a company as a security consultant and are most like a Blue team.
Penetration tester skills required
A penetration tester must be able to modify existing exploits in order to make them work in specific networks for testing purposes. But no single tester can possibly be an expert across all domains, but they need to be active learners and develop real-world experiences.
Understanding of secure web communications and technologies
You need an understanding of web technologies. Web applications are a well-accepted portion of just about every assessment we do these days, and everybody needs to understand them.
Our assessors need to know how web applications are built, how to identify input fields, and how to gather the information that can lead to exploiting the functionality of the web application.
You might also like Top 6 best OS for penetration testing
Ability to Script or Programming
Learning programming is the very first way to start learning about security. There are a lot of languages, most people start with Python, which is the easiest and most popular one.
PHP and Go are the less popular to write security-related stuff, but any of these can still be used in such a context. Bash and PowerShell are mostly about scripting and writing simple CLI applications.
Programming language
- Python
- Ruby
- Perl
- Go
- C/ C++/ C#
You might also like 6 most common mistakes that every beginner should avoid for the best result
Content Management Systems
First, a CMS is computer software used to manage the creation and modification of digital content. Digging into the functionalities and security of CMSs will open your door to a better understanding of how you can manage when in front of one below:
- WordPress
- Joomla
- Drupal
- SPIP
Steps of Penetration Testing
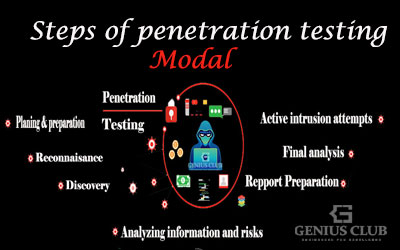
Before the tester starts the vulnerability analysis of a system, there are some crucial steps that he must follow. Each step is important in order to elaborate on a good report after finishing the work.
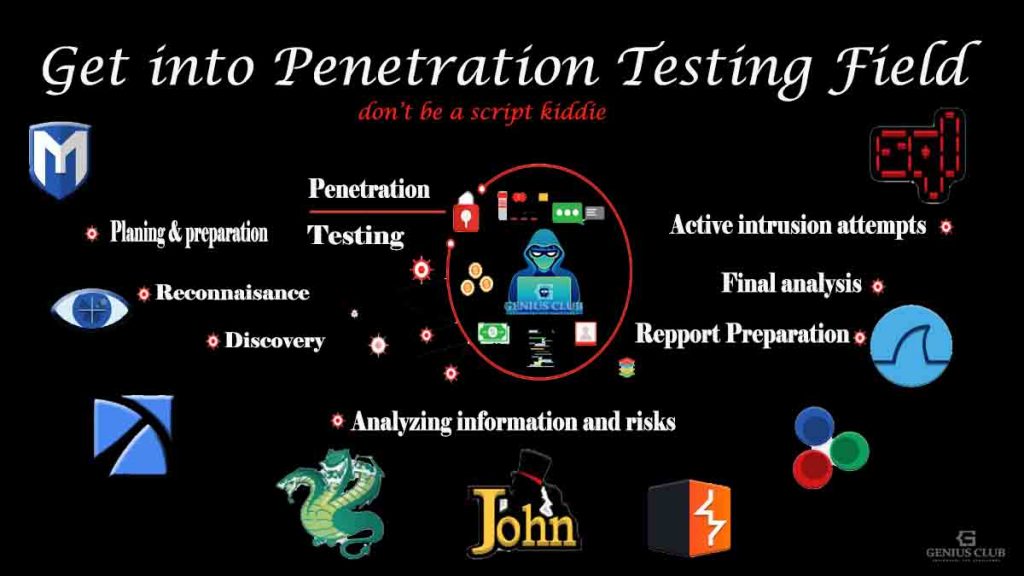
- Planning and preparation
- Reconnaissance
- Discovery
- Analyzing information and risks
- Active Intrusion Attempts
- Final Analysis
- Report Preparation
You can also read more about penetration method
Penetration testing tools

The Kali Linux penetration testing platform contains a vast array of tools and utilities. From information gathering to final reporting, Kali Linux enables security and IT professionals to assess the security of their systems.
Additional resources
Also, here are some other additional resources that will help you in your journey of becoming a pentester.
- Kali Linux documentation
- Lanmaster53
- Darknet
- SANS Penetration Testing Blog
- DigiNinja
- Ethical Hacking LinkedIn Group
- Kitploit
Notice: These resources are not only that you can use. But know that there are many resources over the internet and also books that can help you.


Ok merci beaucoup pour votre soutien
Pingback: How to install D-TECT best termux hacking tool - Tgeniusclub
Pingback: Easy hack Termux tool to exploit android device - Tgeniusclub
Pingback: Unlocking the Potential of Your Smartphone for Ethical Hacking - Tgeniusclub
Pingback: Kali Linux vs Parrot, Which one is the best for pentesting? - Tgeniusclub
Pingback: How to install Onex on termux, the best hacking tool - Tgeniusclub
Pingback: 6 Best Linux distribution for Hacking and Penetration Testing