How to access the dark web safely and wisely
9 min read
Did you know that the internet is much bigger than what you see on Google? In fact, Google only shows a tiny fraction of what’s out there. The internet is made up of different layers, and the part that you use every day is just the tip of the iceberg. Let’s explore the different layers of the web, including the Surface Web, the Deep Web, and the Dark Web.
The dark web has a reputation for being a mysterious and dangerous place, filled with illegal activities, hackers, and cybercriminals.
However, it is also a place where individuals can find information and communicate anonymously, without fear of censorship or persecution.
To access the dark web safely and wisely, it is important to understand the risks involved and take precautions to protect yourself.
This article provides a comprehensive guide to accessing the dark web safely, including tips on how to protect your anonymity, browse safely, and avoid scams and illegal activities.
What are the Layers of the Web?

Before we dive into the Dark Web, let’s talk about the different layers of the web. The Surface Web is the part of the web that most people use every day.
You can find websites through search engines like Google or by typing in a URL. This is where you can shop online, read the news, and connect with friends on social media.
But there are also two other layers of the web, the Deep Web and the Dark Web.
The Surface Web
The Surface Web is the part of the web that’s easily accessible through search engines and web browsers. It’s estimated that the Surface Web makes up only about 4% of the entire internet.
This means that there’s a lot more out there that you can’t find on Google.
The Deep Web
The Deep Web is the part of the web that’s not easily accessible through search engines. This includes things like private databases, online banking, and other secure websites that require a login.
It’s estimated that the Deep Web makes up about 90% of the entire internet. So, while you might not be able to access it easily, it’s a huge part of the web.
Understanding the Dark Web
What is the Dark Web?
The Dark Web is a part of the internet that’s intentionally hidden and not easily accessible. It’s often used for illegal activities like buying and selling drugs, weapons, and stolen information.
The Dark Web is accessed through special software that allows users to remain anonymous and untraceable.
It’s important to remember that the Dark Web is not a safe place to explore, and you should never try to access it without proper guidance and supervision.
Accessing the dark web is easier than you might think. Google only indexes a tiny fraction of the internet. By some estimates, the web contains 500 times more content than what Google returns in search results.
To most users, the internet is what they experience through their email client and web browser every day, but there are a number of expansive services that operate in the background, and the “web” is just one part of it.
Behind that web browser, there are multiple layers that the average user may encounter tangentially or never.
The three parts commonly used to divide the web are the Surface Web, the Dark Web, and the Deep Web.
What’s on the Dark Web?
Believe it or not, there are some websites on the dark web that offer harmless activities and content. For example, you might find a website that provides complex riddles or a book club that makes e-books look more professional.
There are even forums for people who believe free speech is threatened.
However, the dark web is mostly known for its illegal and disturbing content. Here are some examples of what you might find:
- Stolen information: This includes things like credit card numbers, social security numbers, and other personal information that has been stolen from people.
- Illicit substances: You can find drugs like cocaine, heroin, and methamphetamine on the dark web.
- Disturbing and dangerous items: This includes things like weapons, fake IDs, and even hitmen for hire.
- Hacking services: You can hire someone on the dark web to hack into a website or social media account.
It’s important to remember that accessing the dark web can be dangerous and illegal. It’s best to stay away from it altogether and stick to the regular internet.
Dark Web Services
The Dark Web is a part of the internet that is not easily accessible and is often used for illegal activities. However, not all services on the Dark Web are illegal. Here are some of the services available:
Darknet Market
Darknet markets are online marketplaces where people can buy and sell goods anonymously. These markets often sell illegal items such as drugs, weapons, and stolen data. It is important to note that using these markets is illegal and can lead to serious consequences.
Communications
The Dark Web also offers communication services that are encrypted and anonymous. These services are often used by people who want to keep their conversations private.
However, these services can also be used by criminals to plan illegal activities.
File Storage
File storage services on the Dark Web allow users to store files anonymously. These services are often used by people who want to keep their files private or who are worried about government surveillance.
However, these services can also be used to store illegal files such as pirated movies or stolen data.
News & Document
The Dark Web also has websites that offer news and documents that are not available on the regular internet.
These websites often focus on topics that are controversial or illegal. It is important to be cautious when accessing these websites as they may contain illegal content.
Dark Web services
| Darknet market | Communications |
| Agora, AlphaBay | Briar (software) |
| Atlantis, Black Market | Cryptocat, ProtonMail, |
| Dream Market, Evolution | Ricochet (software) |
| The Farmer’s Market, Hansa, Silk Road, | Keybase, SIGAINT |
| Sheep Marketplace, Utopia | TorChat, Tor Mail |
| Operating Systems | Drop sites |
| Tails OS, Debian, Qubes OS | GlobaLeaks, Ljost |
| Social Media | Software |
| facebookcorewwwi.onion, The Hub, Dread, HackBB | Guardian Project, Mailpile |
| File storage | News & document |
| Free Haven | archive.today |
| The Pirate Bay | BBC News |
| Freedom Hosting | DeepDotWeb |
| KickassTorrents | Deutsche Welle |
| Riseup | Doxbin, Wikipedia |
| Nonprofit organization | Search engines |
| Courage Foundation | Ahmia, DuckDuckGo |
| | |
| | |
The Risks Involved in Accessing the Dark Web
Malware and Viruses
One of the biggest risks of accessing the Dark Web is the potential exposure to malware and viruses.
Websites on the Dark Web are often not screened or regulated and may contain malicious code designed to infect computers and steal information.
Hackers and Cybercriminals
The Dark Web is a haven for hackers and cybercriminals who use it to sell stolen data, engage in illegal activities, and launch attacks on unsuspecting users.
Hackers can also use the Dark Web to target users with phishing scams that can compromise their personal and financial information.
Law Enforcement and Legal Consequences
Accessing the Dark Web can expose users to legal consequences, as many of the activities that take place there are illegal.
Law enforcement agencies around the world are increasingly cracking down on Dark Web users, and individuals caught engaging in illegal activities can face severe legal repercussions.
Protecting Your Anonymity on the Dark Web
How to Access the Dark Web Safely
Using Tor
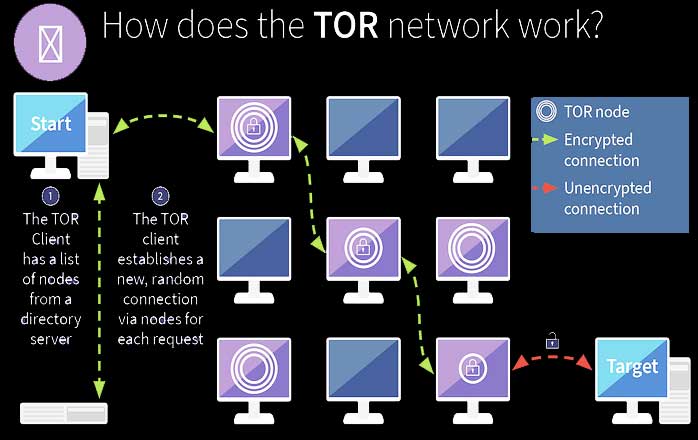
Tor is the most commonly used software for accessing the Dark Web and provides a high level of anonymity by encrypting your internet traffic and bouncing it around a series of servers.
However, it is not foolproof, and users should take additional precautions to protect their anonymity.
Step 1: Download the Tor Browser
The first step to accessing the dark web is to download the Tor browser. This browser is designed to protect your privacy and keep you anonymous while you browse the internet. You can download it for free from the Tor Project website.
To access the vast majority of the dark web, you’ll need a Tor browser. Tor browser is the best powerful anonymous browser and is completely free and open-source software built around onion routing.
The privacy browser Tor protects you by sending your internet traffic and communications around a distributed network of relays run by volunteers all around the world.
Required: How to get and install the Tor browser for online privacy and anonymity
Step 2: Use a VPN
Using the Tor browser won’t make you fully anonymous when surfing on the internet because Tor node IPs are public.
Although websites can’t identify you and ISPs can’t decrypt your traffic, they can see that Tor is being used. Then when using a VPN, your ISP won’t be able to see that you are connected to a Tor node, only an encrypted tunnel to a VPN server.
A VPN, or virtual private network, is a tool that encrypts your internet connection and hides your IP address. This makes it harder for anyone to track your online activity.
Using a VPN is especially important when accessing the dark web because it adds an extra layer of security.
There are many VPN services available, but make sure to choose a reputable one.
Why Use Tor and VPN Together?
While Tor and VPN both offer anonymity, they work in different ways. By using them together, you can add an extra layer of security and privacy to your online activity.
When you use Tor and VPN together, your internet traffic is encrypted twice, making it even more difficult for anyone to track your online activity.
Benefits of Using Tor and VPN Together:
- Increased anonymity and privacy
- Protection against hackers and cybercriminals
- Access to the Dark Web without compromising your identity
Step 3: Be Careful What You Click On
The dark web is full of scams and malicious websites. Be careful what you click on and only visit websites that you trust. Avoid clicking on links that look suspicious or too good to be true.
How to Explore the Dark Web Wisely
Step 1: Stick to Legitimate Websites
As we mentioned earlier, not everything on the dark web is illegal. There are also legitimate websites that use the dark web to protect their users’ privacy.
Stick to these websites and avoid anything that looks suspicious or illegal.
Step 2: Don’t Share Personal Information
Never share your personal information on the dark web. This includes your name, address, phone number, and email address.
The dark web is not a safe place to share personal information, and doing so could put you at risk.
One of the golden rules to use the dark web is to never reveal your real identity. Hence, create a fake identity by using a pseudonym and a fake email address.
Also, be careful not to use the same usernames or passwords on the dark web, as these can be easily linked to your real identity.
Step 3: Use Common Sense
Finally, use common sense when exploring the dark web. If something seems too good to be true, it probably is. If a website looks suspicious, don’t visit it. And also, if you ever feel uncomfortable or unsafe, leave the dark web immediately.
Staying on the Right Side of the Law
Accessing the dark web is not illegal per se. However, engaging in illegal activities is illegal and can lead to severe consequences.
Therefore, stay on the right side of the law by avoiding pornography, drugs, weapons, and other illegal activities.
Remember that the dark web is not a playground, but a place that requires caution and wisdom. In conclusion, the dark web offers a unique and often misunderstood space for individuals to explore and communicate anonymously.
However, it is important to understand the risks and take necessary precautions to stay safe and avoid illegal activities. By following the guidelines outlined in this article, you can access the dark web safely and wisely.
Remember to protect your anonymity, use safe browsing practices, and report any illegal activities you may encounter.
You may also like to know 6 best anonymous browsers





3 thoughts on “How to access the dark web safely and wisely”
Comments are closed.