Hey there! In our last article, we talked about how to hack a Wi-Fi password using a dictionary attack. Today, we’re going to discuss how to use RouterSploit to analyze vulnerabilities.
Why is RouterSploit Important?
Routers are a prime target for network attacks, which can lead to the theft of money and data while bypassing local protection systems. By using free utilities and online test services, you can personally check the quality of firmware and adequacy of settings.
RouterSploit is a powerful tool that can help you discover your network’s vulnerabilities before a hacker does.
If a hacker gains access to your device, they can modify it and access any information they want. That’s why it’s important to use RouterSploit to discover your devices’ vulnerabilities.
By using the vulnerable CWMP implementation, an attacker could do practically anything, such as setting and reading the configuration parameters, resetting parameters to their default values, and remotely rebooting the device.
The most common type of attack is to substitute DNS addresses in the router settings for addresses of servers controlled by the attacker. They filter the web requests and redirect those addressed to banking services to fake pages.
The fake pages have been created for all popular payment systems, such as PayPal, Visa, MasterCard, QIWI, and others.
Why should you use RouterSploit?
It’s clear that there are always some bad practices that users do when it comes to security. By using RouterSploit you can be the first to discover your Network vulnerability before a hacker discovers it. To discover your device’s vulnerabilities, RouterSploit is powerful for that reason why you should use it.
As you know, if a hacker arrives to hack your device, that means he can have access to your network. He can also do any modification and can also get some information he wants.
What is RouterSploit?

The RouterSploit is an open-source exploitation framework dedicated to embedded devices. Also, it consisted of various modules that aid penetration testing operations:
- exploits – modules that take advantage of identified vulnerabilities
- creds – modules designed to test credentials against network services
- scanners – modules that check if a target is vulnerable to any exploit
- payloads – modules that are responsible for generating payloads for various architectures and injection points
- generic – modules that perform generic attacks
Who can install this tool?
Before we go to the installation, we have to make sure everyone knows if you have what is required.
Requirements
- future
- requests
- paramiko
- pysnmp
- pycrypto
We are going to see how you can install RouterSploit on kali-Linux, Ubuntu 20.04, Ubuntu 18.04, OSx, Docker, and Termux. Now we are going to start with the installation process, we are going to use some basics Linux commands if you are not familiar with Linux you can look at this article Linux for beginners.
We’re going to show you how to install RouterSploit on Kali-Linux, Ubuntu 20.04, Ubuntu 18.04, OSx, Docker, and Termux. We’ll be using some basic Linux commands, so if you’re not familiar with Linux, check out this article on Linux for beginners.
How to install RouterSploit on kali Linux?
Now, the first step is to install python3 pip, open your Kali Linux terminal then type the command,
apt-get install python3-pipThen, after that, you can clone RouterSploit from GitHub by using the command. First, you have to choose the destination where you want to store RouterSploit.
git clone https://www.github.com/threat9/routersploitNow, navigate to the RouterSploit folder with the command:
cd routersploitThen, we are going to install requirements.txt using python3.
python3 -m pip install -r requirements.txt
then use
python3 rsf.pyFor Bluetooth Low Energy support, use the following commands:
apt-get install libglib2.0-dev
python3 -m pip install bluepy
python3 rsf.py
How to install RoiterSploit on Ubunu 20.04?
The first step is to install python3 pip. Open your Ubuntu terminal and type the command:
sudo apt-get install git python3-pipNext, clone RouterSploit from GitHub using the command below. Choose the destination where you want to store RouterSploit:
git clone https://www.github.com/threat9/routersploitNow, you have to navigate to the RouterSploit folder with the command.
cd routersploitThen, install requirements.txt using python3.
python3 -m pip install -r requirements.txt
then use
python3 rsf.pyFor Bluetooth Low Energy support, use the following commands:
apt-get install libglib2.0-dev
python3 -m pip install bluepy
python3 rsf.py
How to install RoiterSploit on Ubuntu 18.04 & 17.04?
The first step is to install python3 pip. Open your Ubuntu terminal and type the command:
sudo add-apt-repository universe
sudo apt-get install git python3-pipNext, clone RouterSploit from GitHub using the command below. Choose the destination where you want to store RouterSploit:
git clone https://www.github.com/threat9/routersploitNow, you have to navigate to the RouterSploit folder with the command.
cd routersploitThen, we are going to install requirements.txt using python3.
python3 -m pip install -r requirements.txt
then use
python3 rsf.pyFor Bluetooth Low Energy support, use the following commands:
apt-get install libglib2.0-dev
python3 -m pip install bluepy
python3 rsf.py
Usage of RouterSploit
After installation, use the command “Routersploit” to run this tool. To list all the RouterSploit options, use the command “show all“. This will display a long list of features that allow you to perform all kinds of actions to breach routers and other devices capable of connecting to the network, such as security cameras. Take a few minutes to explore and see how no manufacturer is immune to vulnerabilities.
If you want to test a particular router, choose the order and use the command “scanners/autopwn”. Then, use the command “show options” to see the available options.
Now, after the installation, you can use the command Routersploit to run this tool.

To list all the RouterSploit options, just use the command show all.
A very long list of all the features of Routersploit will appear, each, in turn, allows you to perform all kinds of actions to breach routers. Likewise, other devices capable of connecting to the network such as security cameras can be exploited by this framework. Take a few minutes, and you will see how no (especially reputable) manufacturer is immune to vulnerabilities.

Then, if we want to test a particular router, we have to choose the order.
use scvanners/autopwnNow, we use the command:
show options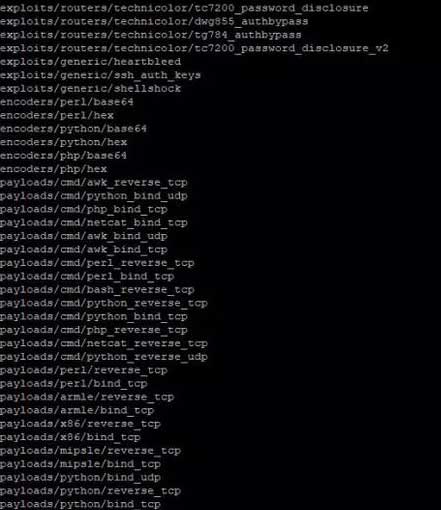
As you have seen, it is extremely easy to find a way to breach multiple devices with just RouterSploit. Also, you don’t need a computer or a specialized server for this, remember that, especially Kali Linux distributions, can be used live. So there are more possibilities for a cybercriminal to take control of devices such as Wi-Fi routers.
However, depending on each country, if you try to exploit vulnerabilities and take control of a device that is not originally managed by you, you could face some very serious legal issues. Today, we have many options for network devices that we can purchase so that we can set up a small lab in our homes.


Hello there I am so glad I found your website, I really found you
by accident, while I was looking on Google for something else,
Regardless I am here now and would just like to say thanks a lot for
a marvelous post and a all round enjoyable blog (I also love the theme/design), I don’t have time to browse it all at the moment but I
have bookmarked it and also included your RSS feeds, so when I
have time I will be back to read a great deal more,
Please do keep up the fantastic b.
thanks
I’ll immediately snatch your rss as I can’t find your email subscription link or e-newsletter service.
Do you’ve any? Please permit me know in order that I could subscribe.
Thanks.
Everything is very open with a precise description of the
challenges. It was definitely informative. Your website is very useful.
Thank you for sharing!
Thanks for one’s marvelous posting! I certainly enjoyed reading it, you
happen to be a great author.I will be sure to bookmark your blog and
will often come back down the road. I want to encourage you to definitely continue your great work, have
a nice afternoon!
Pingback: Mrphish best termux tool to hack social media account - Tgeniusclub