How to prevent smartphones attacks?
The world with advanced technology has become great and sometimes harmful. At the end of the day, everything is hackable. What I am surprised about is that people sometimes forget that it’s so easy to hack into their devices. Said Adi Sharabani, the co-founder of mobile security company Skycure, who used to work for Israeli Intelligence.
Hackers can get into your phone without even your knowledge. Human vulnerabilities are giving hackers access to many devices without touching the victim’s device. Day and night, smartphone brand providers are working on how to secure their provided smartphones in such a way that hackers are also testing vulnerabilities day and night.
Also, the threat of having your phone hacked has become a common and rational fear. The cold, hard truth is that it is now possible to hack any phone.
With the advancement of technology, where the discovery of knowledge and information advances the understanding of technology, hackers are able to hack even some of the most sophisticated phone software.
Unfortunately, there are many hackers with malicious intent that can and do break into an Android device to steal valuable personal information or profit from illegal financial transactions. While it may be hard (or even impossible) to make your Android unhackable, there are things you can do to make your device more secure.
We wrote a blog post for you to know if your smartphone is tapped or spied
Example of hacking attacks
- Malware attack
- Phishing attack
- SQL Injection Attack
- Cross-Site Scripting (XSS)
- Denial of Service (DoS)
- Session Hijacking and Man-in-the-Middle Attacks
- Credential Reuse
Malware
If you’ve ever seen an antivirus alert pop up on your screen, or if you’ve mistakenly clicked a malicious email attachment, then you’ve had a close call with malware. Attackers love to use malware to gain a foothold on users’ computers and, consequently, the offices they work in because it can be so effective.
In the same way, attackers will use a variety of methods to get malware into your computer, but at some stage, it often requires the user to take some action to install the malware.
As well, this can include clicking a link to download a file, or opening an attachment that may look harmless (like a Word document or PDF attachment), but actually has a malware installer hidden within.
Phishing attack
When an attacker wants you to install malware or divulge sensitive information, they often turn to phishing tactics, or pretending to be someone or something else to get you to take an action you normally wouldn’t. Since they rely on human curiosity and impulses, phishing attacks can be difficult to stop.
So, in a phishing attack, an attacker may email you that appears to be from someone you trust, like your boss or a company you do business with. The email will seem legitimate, and it will have some urgency to it (e.g., fraudulent activity has been detected on your account).
In the email, there will be an attachment to open or a link to click. Upon opening the malicious attachment, you’ll thereby install the malware on your device.
If you click the link, it may send you to a legitimate-looking website that asks for you to log in to access an important file. Except the website is actually a trap used to capture your credentials when you try to log in.
To reduce the risk of being phished, you can use these techniques:
- Critical thinking: do not accept that an email is the real deal just because you’re busy or stressed, or you have 150 other unread messages in your inbox. Stop for a minute and analyze the email.
- Hovering over the links: Move your mouse over the link, but do not click it! Just let your mouse cursor hover the link and see where you would actually take you. Apply critical thinking to decipher the URL.
- Analyzing email headers: Email headers define how an email got to your address. The “Reply-to” and “Return-Path” parameters should lead to the same domain as is stated in the email.
- Sandboxing :You can test email content in a sandbox environment, logging activity from opening the attachment or clicking the links inside the email.
Hacking Software
Did you know that hacking software for Android and other mobile devices exists? And did you know there are countless hacking software options online for free? Hacking software is a method used by hackers to get information from a phone.
Despite the price of hacking software, serious hackers can buy hacking software anywhere, such as a phone spy app, which must be installed on the target phone. Not all hackers need to handle the victim phone physically to install hacking software. But in some cases, they must.
Keyloggers are a type of monitoring software designed to record keystrokes made by a user. One of the most traditional types of cyber threat, these keystroke loggers record the information you type into a website or application and send it back to a third party.
It can be installed in your phone to record all information you type on your keyboard and send it to a third party set by the hacker.
A Trojan horse, or Trojan, is a type of malware that is often disguised as legitimate software. Cyber-thieves and hackers can be employed by cuber-thieves and try to gain access to users’ systems.
Users are typically tricked by some form of social engineering into loading and executing Trojans on their systems. Once activated, Trojans can enable cuber-criminals to spy on you, steal your sensitive data, and gain backdoor access to your system.
Hacker use phishing to impress victim to install Trojans in their devices. These actions can include:
- Deleting data
- Blocking data
- Modifying data
- Copying data
- Disrupting the performance of computers or computer networks

Spyware is a type of program that is installed to collect information about users, their computers, or their browsing habits. It tracks everything you do without your knowledge and sends the data to a remote user.
It also can download and install other malicious programs from the internet. Spyware works like adware, but is usually a separate program that is installed unknowingly when you install another freeware application.

Also, a spy is an excellent tool for hacking someone’s phone by number, is the outstanding one among all other telephone number programmer applications at any point imagined.
More than a million clients in 190+ nations depend significantly on the form. The app can hack somebody’s mobile phone by simply their number if they’re utilizing an Android or iOS gadgets.

SIM Card Hacking
In August 2019, the CEO of Twitter had his SIM card hacked by SIM card swapping using the phishing method. SIM card swapping is performed when the hacker contacts your phone provider, pretends to be you, and then asks for a replacement SIM card.
Once the provider sends the new SIM to the hacker, the old SIM card will be deactivated, and your phone number will be stolen. This means the hacker has taken over your phone calls, messages, etc.
This method of hacking is relatively easy if the hacker can convince the provider that they are you. Keeping personal details to yourself is an important part of ensuring that hackers cannot pretend to be you.
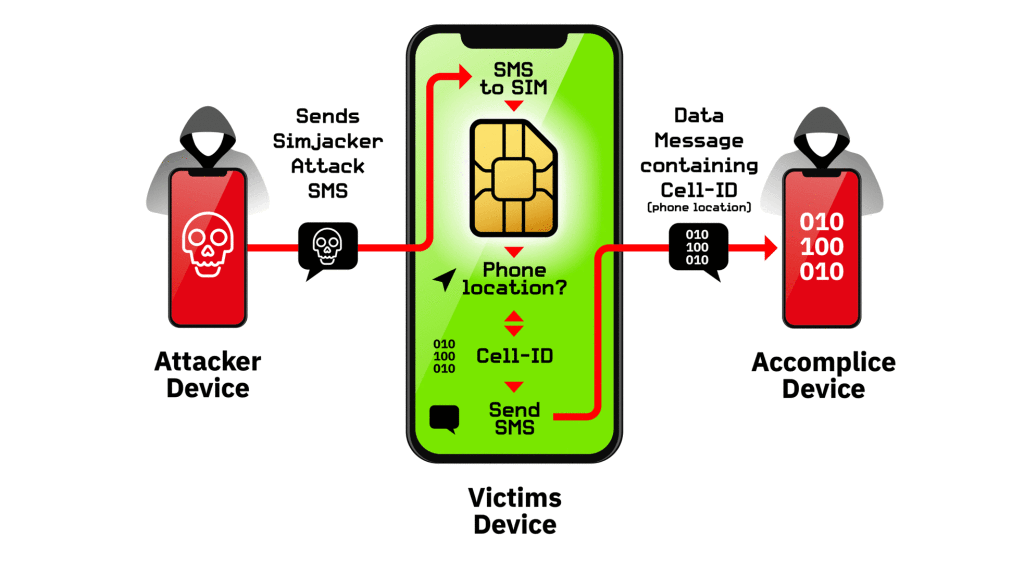
In addition, Adaptive Mobile Security discovered a new way hackers were getting into phones using the SIM card—a method they call Simjacker. This method of hacking is more complex than phishing, as it targets a SIM card by sending a signal to the target device. If the message is opened and clicked on, hackers are able to spy on the hacked device and even find out the location of the device.
Bluetooth Hacking
In the same way, professional hackers can use special software products to search for vulnerable mobile devices with an operating Bluetooth connection. These types of hacks are done when a hacker is in range of your phone, usually in a populated area.
Then when hackers are connected to your Bluetooth, they have access to all the information available and the internet connection to access the web, but the data must be downloaded while the phone is within range.
How to Prevent to become a victim of phone hacking
As you saw, there are many techniques and tools hackers can use to hack your devices. Here are a few tips to ensure that you are not a victim of phone hacking:
1. Avoid sharing your phone with untrusted people
On the other hand, the easiest way for a hacker to steal your phone’s information is to gain access to it. Therefore, it is always important to avoid sharing your phone with untrusted people.
If you have been away from your phone around a group of strangers and are concerned about possible hacking, check your settings and look for strange apps.
2. Do encryption of Your Device
Also, encrypting your cell phone can protect you from being hacked and can protect your calls, messages, and critical information. To check if a device is encrypted, iPhone users can go into Touch ID & Passcode, scroll to the bottom, and enable Data protection. Android users have automatic encryption depending on the type of phone.
3. lock your SIM Card
addionally Putting a passcode on your SIM card can protect it from being hacked.
4. Check your WIFI and Bluetooth
It is fairly easy for hackers to connect to your phone using Wi-Fi or Bluetooth if they are on, so turn them off when not needed because there is no warning when a hacker attacks you.
If you fear being hacked in a public space, turning off your phone can block a hacker’s ability to hack you, this is an effective preventative method.
5. Use Security Protection or installing an anti-malware
Protecting your device from hackers require some knowledge that you have already. Use device provide security or installing a antivirus or a anti-malware in your device will block some untrusted app or websites.
Closing word
Making a point to understand how hacking works can help you practice security in your every day life. Know how to be prepared for being hacked, so that when it happens you can be on top of how to handle it.


Message
good
07510616512
Pingback: How to know if Your smartphone is Tapped or spyed - tgeniusclub
Pingback: How to protect Facebook account from hackers. Best technics - tgeniusclub
Trop cool
Merci beaucoup vraiment
Vous venez de créer une vigilance dans moi
Nice information bro.
You website is cool and it is the source of hacking information.
Thanks for building this.
Thanks also. If any suggestions about the following article don’t hesitate to let me know
Pingback: How to protect your smartphone from hackers - Tgeniusclub
Fantastic
Fantastic